The domain name system has become an important part of our daily lives. "Dot-com" is a symbol of high-powered e-commerce. As with any category system, the divisions of the DNS shape our conception of the Internet, dividing web sites into those that are commercial, governmental, or foreign. Yet despite this strong presence, the DNS has a tangled past, and its current management is still subtly contested.
The Internet began as in 1969 as ARPANET, which was a project of the US Department of Defense's Advanced Research Projects Agency (ARPA). Other host computers that used the TCP/IP network protocol could also join this initial network, though at the time this meant mainly research and educational institutions. The National Science Foundation (NSF) funded much of the commercial and non-military backbone of this early network.[1,2]
Each computer, or host, on a TCP/IP network has a unique 32-bit number associated with it. This is referred to as its "IP address" or "IP number." Though these number work well for computers, people find them very difficult to remember. During this early time of the Internet, a single HOSTS.TXT file was hosted by the Network Information Center (NIC) at the Stanford Research Institute (SRI). [3] Each new host that joined the network would submit its name and corresponding IP number to be added to HOSTS.TXT. Every couple days, each host on the network would download a copy of this file. In this way, people could enter an easy-to-remember name, and their local computer would check this against the recently downloaded version of HOSTS.TXT to determine the corresponding IP number. Then this number could be used by the computer to establish a connection to the desired destination.
This system quickly developed problems, however. Each new host on the network meant another entry in HOSTS.TXT, producing a bigger file and a longer download for everyone. Even worse, the SRI-NIC computer was the sole source of the authoritative file. Each new host meant another download from SRI-NIC. As the Internet grew, SRI-NIC did not have the bandwidth it needed to maintain the system. [4,5]
In 1983, a group of people -- including Dr. Jon Postel and Paul Mockapetris at the University of Southern California's (USC) Information Sciences Institute (ISI) -- proposed a new decentralized system. This was the beginning of the Domain Name System (DNS), which is still used today.
By 1985, the DNS was implemented. The Department of Defense delegated authority over IP numbers and the new domain name space to the new Internet Assigned Numbers Authority (IANA). An influential member of IANA was Jon Postel, who had been largely responsible for overseeing the delegation of IP numbers in the past. Though IANA supervised the name space, NSF entered an agreement with Network Solutions, Inc. (NSI) to handle the actual registering of domain names. [6]
This worked quite well for a time. By 1994, however, there was a general feeling of discontent with the system. NSI held a monopoly over domain name registration. It charged $50 per year for each name registered. It frequently sided with trademark owners in any dispute over a domain name, leaving domain name holders with little recourse. There was also a call for more top level domains besides the current standards such as .com, .edu, and .net.
There followed a period of much debate and numerous proposals. The US government was closely involved and a Green Paper and a White Paper were released with possible solutions. Some of the groups involved were: World Intellectual Property Organization (WIPO), the Patent and Trademark Office (PTO), the Federal Communication Commission (FCC), the International Trademark Association, the Internet Society, the US Departments of Defense, State, Justice, and Commerce, and others.[7] Several associations and committees were formed to suggest alternatives.
Much of the difficulty arose from determining just who held power over the DNS. The Department of Defense had delegated their power over ARPANET to IANA, yet the ARPANET part of the Internet had been dismantled in the late 1980's shortly after DNS went into effect. The National Science Foundation (NSF) had funded most of the commercial backbone of the Internet and had delegated much of their authority to NSI to register domain names. Yet who would have authority if these contracts weren't renewed?
In late 1998, the US Department of Commerce, with cooperation from IANA and NSI, set up the Internet Corporation for Assigned Names and Numbers (ICANN). It is a non-profit organization incorporated in California. Though it was not clear how much authority ICANN would have, its Chief Technical Officer was Jon Postel, who brought with him a large part of the Internet technical community's respect. Sadly, Jon Postel died shortly after ICANN's inception. [8]
NSI was relieved of its domain-name-selling monopoly position and instructed to now renew its contract through ICANN. Other domain name registrars begin to appear, fostering competition and driving down the price of domain names. Though business continued as usual, ICANN was, and still is, left in something of a precarious position. Many people question its authority over an international domain space, and whether it is even accountable to the Internet community. It is not even clear whether ICANN is supposed to implement policy or is to merely act as a technical advisory body.
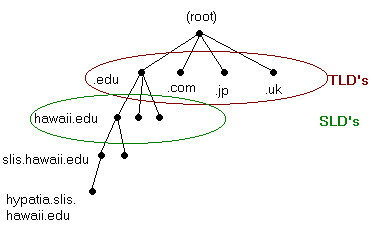
The Domain Name System is structured similarly to the file system used by most operating systems. It has an inverted tree structure. Each node is formed by one or more computers. At the root there are 13 computers that each host identical copies of a single file. This file gives the addresses of the servers that are authoritative for the 252 Top Level Domains (TDLs) [9]. Top Level Domains are divided into two groups: generic Top Level Domains (gTLDs) and country code Top Level Domains (ccTLDs). The gTLDs are .com, .org, .net, .edu, .gov, .mil, and .int. (Seven more gTLDs have recently been approved for use, but they have not yet been implemented.) The ccTLDs are two-letter codes for each country. Examples include Japan's .jp, the United Kingdom's .uk, and South Africa's .za. [10]

Each level can delegate authority for parts below it. For example, the server authoritative for .edu does not need to know the address for ics.hawaii.edu or slis.hawaii.edu. If hawaii.edu is authoritative for its zone of the domain system, then the .edu server needs only know the address for hawaii.edu and refer all inquiries there.
An example of how the system works may make this clearer. Suppose a user types the address "hypatia.slis.hawaii.edu" into their web browser. To connect to this destination server, the browser needs to know the corresponding IP address. A name resolver, running either on the user's computer or on the server through which they are connected, sends a query to the root of the DNS. The root doesn't know the IP address; it only knows the address for the servers authoritative for TLDs. But it knows that the resolver will have to go through the .edu domain. So the root sends back the address for the .edu domain server. With this information, the user's computer can now contact the .edu domain server. The .edu server doesn't know the desired IP address, but it knows which computer is authoritative for hawaii.edu, so it returns that address. The resolver can now query hawaii.edu, whose best guess is the slis.hawaii.edu server. The resolver queries slis.hawaii.edu. Slis.hawaii.edu does know the IP address for hypatia.slis.hawaii.edu and returns it: 128.171.58.11. Armed with this, the user's browser can now make the connection.
This example is simplified somewhat. There are actually multiple computers at each node of the DNS that mirror the same information. Also, the resolver or the browser may have been to hawaii.edu recently, and so still have its IP address in its cache. If so, it may start the resolving search there, rather than at the DNS root. But the basic path followed and the end result are the same.
As it can be seen from the structure of DNS, the root is incredibly important. If the root was destroyed, domain name resolution would cease. (It would likely take a couple days for all resolving to stop, as a great number of addresses will still be in various server caches around the world.) This is an unlikely occurrence, however, since there are thirteen protected servers around the world that are authoritative root servers.
What is more of a concern is who controls those servers on a daily basis. Or, more importantly, the information they relay. The thirteen root servers are actually owned by a number of different organizations--some commercial, some military--and provide the hosting as a volunteer service. Twelve of the thirteen servers get their information from a main file on an NSI computer. Yet the US Department of Commerce claims that it has authority over this file.[11] In the past, IANA was the organization that made most of the changes to the file.
One reason it is not very clear who controls the root is that it only contains pointers to the 252 TLDs. Changes are made relatively infrequently. A second reason is that it has never been clear. Maintenance has always been on an ad hoc, volunteer, community-minded basis. The US government is probably the de facto owner, since, directly or indirectly, they have been providing the funding for its maintenance, whether through ARPA, NSF, or university grants. [12,13]
However, control over where these pointers go determines who has control over each TLD domain. ICANN is slowly assuming control of the root file. Indeed, according to its own description, is organizes the use of IP numbers, DNS, protocol parameters, and port numbers used on the Internet. [14]
There remains a large debate on whether ICANN has legitimate claim to such root control. It is clear that ICANN now stands in a position to make DNS policy, thereby potentially affecting millions of Internet users. However, despite this power, there is little accountability to the public.
There are two possible sources of legitimacy. One is that the Department of Commerce has granted the US government's authority to ICANN. Admittedly, ICANN has structured itself like a federal agency. However, some people, such as A. Michael Froomkin, point out, this isn't sufficient. If the Department of Commerce is still maintaining its control over DNS policy, then it is illegally by-passing APA (Administrative Procedures Act) regulations. Yet if it has truly delegated authority, then ICANN, a private body, is unconstitutionally exercising public power. In either case, it has none of the checks to its power in place in other governing bodies. [15,16]
The other possibility is that ICANN's power really comes through the consensus of the Internet community, that the Internet public will simply agree to follow ICANN's suggestions. This is what ICANN itself implies, stating that it has no authority beyond what is given by consensus. [17]. To this end, five of their nineteen-member board are elected by the Internet public, though the process is somewhat involved. [18,19,20] At large site; governing]. Even though each of these five members is elected from a separate region of the world, few people have faith that ICANN's current structure can really represent the internet community as a whole [21] or that they can adequately judge whether they have consensus. [22]
As is usually the case, there is a way to sidestep the whole issue: abandon the current DNS all together. In 1997, an organization called AlterNIC briefly stole DNS traffic from InterNIC/NSI--redirecting all traffic to AlterNIC's own site--as a form of protest of NSI's monopoly. Though they did not publicly reveal how they accomplished this, the incident does demonstrate that some control by users is possible, even if only at a guerilla level. [23]
It is also important to keep in mind the common DNS system is only one alternative. Indeed, many others do exist on a smaller scale. One developing system, eDNS, would give registrars the ability to sell new TLDs as easily as they do domain names now. Japan has a separate system to allow for 16-bit characters in their domain names. [24] All that is required to use an alternative DNS system is to point your name resolver to start at a different root server.
It has never been clear who is in control of the Domain Name System. This is because it developed in an very ad hoc way in the community-minded environment of the early Internet. However, now the system is used by a great variety of people, each with their own concerns on how the system is managed. Indeed, it seems that some authoritative body is needed. The question still remains concerning the source of this authority. I think that ICANN, after assuming IANA's role with the backing of the US government, has received all the official DNS authority that previously existed. But there wasn't much to receive! Now ICANN must stand or fall on its own, based on acceptance by the Internet community. Though their electoral system may be imperfect, it is at least in a step in the direction to consensus. If they restrict themselves to technical issues and step carefully, they will likely encounter little resistance. However, if they begin to instate policy, such as ruling in domain name disputes, they will likely feel some backlash. I imagine that, given time and cautious moves, ICANN will eventually become an established organization based on consensus. If not, there's always an alternative DNS to try.
1. Albitz, Paul, Matt Larson, and Cricket Liu. DNS on Windows NT. Cambridge: O'Reilly & Associates, 1998.
2. Weinberg, Jonathan. "ICANN and the problem of legitimacy." Duke Law Journal. 50 (Oct 2000): p187. Online version: <http://web1.infotrac.galegroup.com/itw/infomark/699/508/27643551w3/ purl=rc1_EAI_0_A68148808&dyn=15!xrn_1_0_A68148808?sw_aep=hawaii_hamilton>
3. Albitz, Paul, Matt Larson, and Cricket Liu. DNS on Windows NT. Cambridge: O'Reilly & Associates, 1998.
4. Ibid.
5. Weinberg, Jonathan. "ICANN and the problem of legitimacy." Duke Law Journal. 50 (Oct 2000): p187. Online version: <http://web1.infotrac.galegroup.com/itw/infomark/699/508/27643551w3/ purl=rc1_EAI_0_A68148808&dyn=15!xrn_1_0_A68148808?sw_aep=hawaii_hamilton>
6. Ibid.
7. Ibid.
8. Ibid.
9. Froomkin, A. Michael. "Wrong Turn In Cyberspace: Using ICANN to Route around the APA and the Constitution." <http://www.law.miami.edu/~froomkin/articles/icann-body.htm> Accessed: 06 May 2001.
10. Albitz, Paul, Matt Larson, and Cricket Liu. DNS on Windows NT. Cambridge: O'Reilly & Associates, 1998.
11. Froomkin, A. Michael. "Wrong Turn In Cyberspace: Using ICANN to Route around the APA and the Constitution." <http://www.law.miami.edu/~froomkin/articles/icann-body.htm> Accessed: 06 May 2001.
12. "ICANN: The Debate over Governing the Internet." http://www.law.duke.edu/journals/dltr/ARTICLES/2001dltr0002.html Accessed: 06 May 2001.
13. Froomkin, A. Michael. "Wrong Turn In Cyberspace: Using ICANN to Route around the APA and the Constitution." <http://www.law.miami.edu/~froomkin/articles/icann-body.htm> Accessed: 06 May 2001.
14. "Supporting Organizations." <http://www.icann.org/support-orgs.htm> Accessed: 05 May 2001.
15. Froomkin, A. Michael. "Wrong Turn In Cyberspace: Using ICANN to Route around the APA and the Constitution." <http://www.law.miami.edu/~froomkin/articles/icann-body.htm> Accessed: 06 May 2001.
16. Weinberg, Jonathan. "ICANN and the problem of legitimacy." Duke Law Journal. 50 (Oct 2000): p187. Online version: <http://web1.infotrac.galegroup.com/itw/infomark/699/508/27643551w3/ purl=rc1_EAI_0_A68148808&dyn=15!xrn_1_0_A68148808?sw_aep=hawaii_hamilton>
17. "ICANN Background." <http://www.icann.org/general/background.htm> Accessed: 05 May 2001.
18. "Supporting Organizations." <http://www.icann.org/support-orgs.htm> Accessed: 05 May 2001.
19. "ICANN Frequently Asked Questions." <http://www.icann.org/general/faq1.htm#membership> Accessed: 08 May 2001.
20. "ICANN: The Debate over Governing the Internet." http://www.law.duke.edu/journals/dltr/ARTICLES/2001dltr0002.html Accessed: 06 May 2001.
21. Weinberg, Jonathan. "ICANN and the problem of legitimacy." Duke Law Journal. 50 (Oct 2000): p187. Online version: <http://web1.infotrac.galegroup.com/itw/infomark/699/508/27643551w3/ purl=rc1_EAI_0_A68148808&dyn=15!xrn_1_0_A68148808?sw_aep=hawaii_hamilton>
22. "ICANN: The Debate over Governing the Internet." http://www.law.duke.edu/journals/dltr/ARTICLES/2001dltr0002.html Accessed: 06 May 2001.
23. Macavinta, Courtney. "AlterNIC takes over InterNIC traffic." <http://news.cnet.com/news/0,10000,0-1004-200-320460,00.html> 14 July, 1997.
24. Nobuko. Class presentation. LIS 670. University of Hawaii-Manoa, Honolulu, HI. 30 April 2001.
| ~ztomasze Index:
LIS: The Domain Name System http://www2.hawaii.edu/~ztomasze |
Last Edited: 08 May 2001 ©2001 by Z. Tomaszewski. |